Disclaimer: Information found on CryptoreNews is those of writers quoted. It does not represent the opinions of CryptoreNews on whether to sell, buy or hold any investments. You are advised to conduct your own research before making any investment decisions. Use provided information at your own risk.
CryptoreNews covers fintech, blockchain and Bitcoin bringing you the latest crypto news and analyses on the future of money.
Lazarus employed ‘Kandykorn’ malware in effort to breach exchange, according to Elastic.
The Lazarus Group has employed a new type of malware in an effort to breach a cryptocurrency exchange, as reported by Elastic Security Labs on October 31.
Elastic has designated the new malware as “Kandykorn” and referred to the loader program that introduces it into memory as “Sugarload,” noting that the loader file features a unique “.sld” extension. The specific exchange that was targeted has not been disclosed by Elastic.
Throughout 2023, cryptocurrency exchanges have experienced a series of private-key breaches, the majority of which have been linked to the North Korean cybercrime organization Lazarus Group.
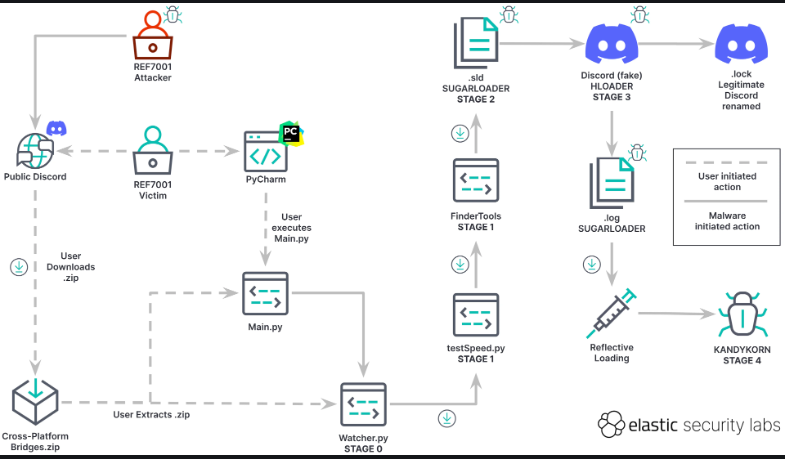 Kandykorn infection process. Source: Elastic Security Labs
Kandykorn infection process. Source: Elastic Security Labs
As per Elastic, the assault commenced when members of Lazarus posed as blockchain engineers and approached engineers from the unnamed crypto exchange. The attackers initiated contact via Discord, asserting that they had developed a lucrative arbitrage bot capable of capitalizing on price discrepancies for cryptocurrencies across various exchanges.
The attackers persuaded the engineers to download this “bot.” The files within the program’s ZIP archive were given misleading names such as “config.py” and “pricetable.py,” which made them appear to be part of an arbitrage bot.
Upon execution of the program by the engineers, it ran a “Main.py” file that executed some benign programs alongside a harmful file named “Watcher.py.” Watcher.py established a link to a remote Google Drive account and began downloading data from it to another file called testSpeed.py. The malicious software then executed testSpeed.py once before removing it to erase its traces.
During the single execution of testSpeed.py, the program downloaded additional data and ultimately ran a file that Elastic refers to as “Sugarloader.” This file was obfuscated using a “binary packer,” according to Elastic, enabling it to evade detection by most malware detection tools. However, they managed to identify it by halting the program after its initialization functions were executed and then capturing a snapshot of the process’s virtual memory.
Elastic conducted a VirusTotal malware scan on Sugarloader, which determined that the file was not malicious.
Related: Crypto firms beware: Lazarus’ new malware can now bypass detection
After Sugarloader was installed on the computer, it connected to a remote server and directly downloaded Kandykorn into the device’s memory. Kandykorn is equipped with various functions that the remote server can utilize to carry out different malicious operations. For instance, the command “0xD3” can be employed to enumerate the contents of a directory on the victim’s computer, while “resp_file_down” can be used to transfer any files from the victim’s device to the attacker’s system.
Elastic estimates that the attack took place in April 2023. They assert that the program is likely still in use for ongoing attacks, stating:
“This threat is still active and the tools and techniques are being continuously developed.”
Centralized cryptocurrency exchanges and applications faced a wave of attacks in 2023. Alphapo, CoinsPaid, Atomic Wallet, Coinex, Stake, and others have fallen victim to these incidents, most of which appear to involve the attacker stealing a private key from the victim’s device and utilizing it to transfer customers’ cryptocurrency to the attacker’s address.
The United States Federal Bureau of Investigation has implicated the Lazarus Group in the Coinex breach, as well as in the Stake attack and other incidents.
