Disclaimer: Information found on CryptoreNews is those of writers quoted. It does not represent the opinions of CryptoreNews on whether to sell, buy or hold any investments. You are advised to conduct your own research before making any investment decisions. Use provided information at your own risk.
CryptoreNews covers fintech, blockchain and Bitcoin bringing you the latest crypto news and analyses on the future of money.
BleepingComputer Discovers New Scheme for Bitcoin Address Substitution, 2026/02/21 13:04:36

Fraudsters have devised a scheme for covertly substituting Bitcoin addresses under the guise of “profitable cryptocurrency arbitrage,” according to analysts from the cybersecurity firm BleepingComputer.
Their findings indicate that the campaign is built on the promise of profits from a purportedly discovered “arbitrage vulnerability” within the digital asset exchange service Swapzone. In practice, the perpetrators deploy malicious code that alters the exchange page directly in the victim’s browser.
“This is one of the first documented instances of social engineering being used to manipulate web pages for the direct theft of cryptocurrency. To promote the campaign, the criminals post comments on the text storage service Pastebin,” the researchers noted.
The fraudsters advertise a “leak of hacking documentation,” claiming potential earnings of up to $13,000 within a few days, and provide instructions that supposedly allow users to receive inflated amounts when exchanging BTC. The instructions suggest that victims should:
-
visit the Swapzone website;
-
copy JavaScript code from an external source;
-
return to the Swapzone tab, enter javascript: in the address bar, paste the copied code, and press Enter.
This technique utilizes the browser’s javascript: URI function, enabling the execution of code directly on the open page. Initially, the main script loads, followed by an obfuscated portion of the code that is injected into the page and alters the transaction execution scripts.
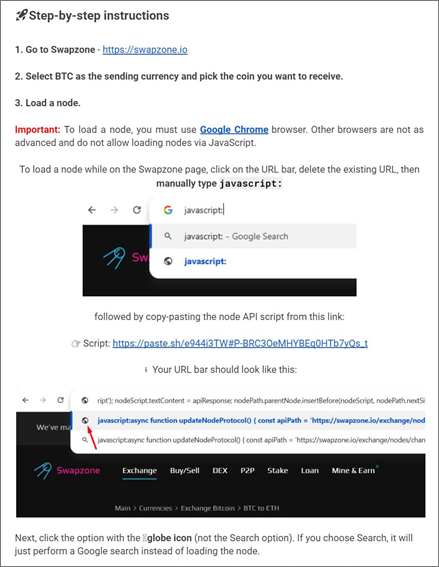
The malicious code substitutes the fraudsters’ Bitcoin addresses and modifies the displayed rates and payout amounts, creating the illusion of a properly functioning “arbitrage scheme.” Consequently, the user sees the familiar interface of the service but sends funds to the criminals’ wallet.
Previously, specialists from the Swiss company Global Ledger reported that criminals have learned to withdraw stolen crypto assets just seconds after compromising wallets.
